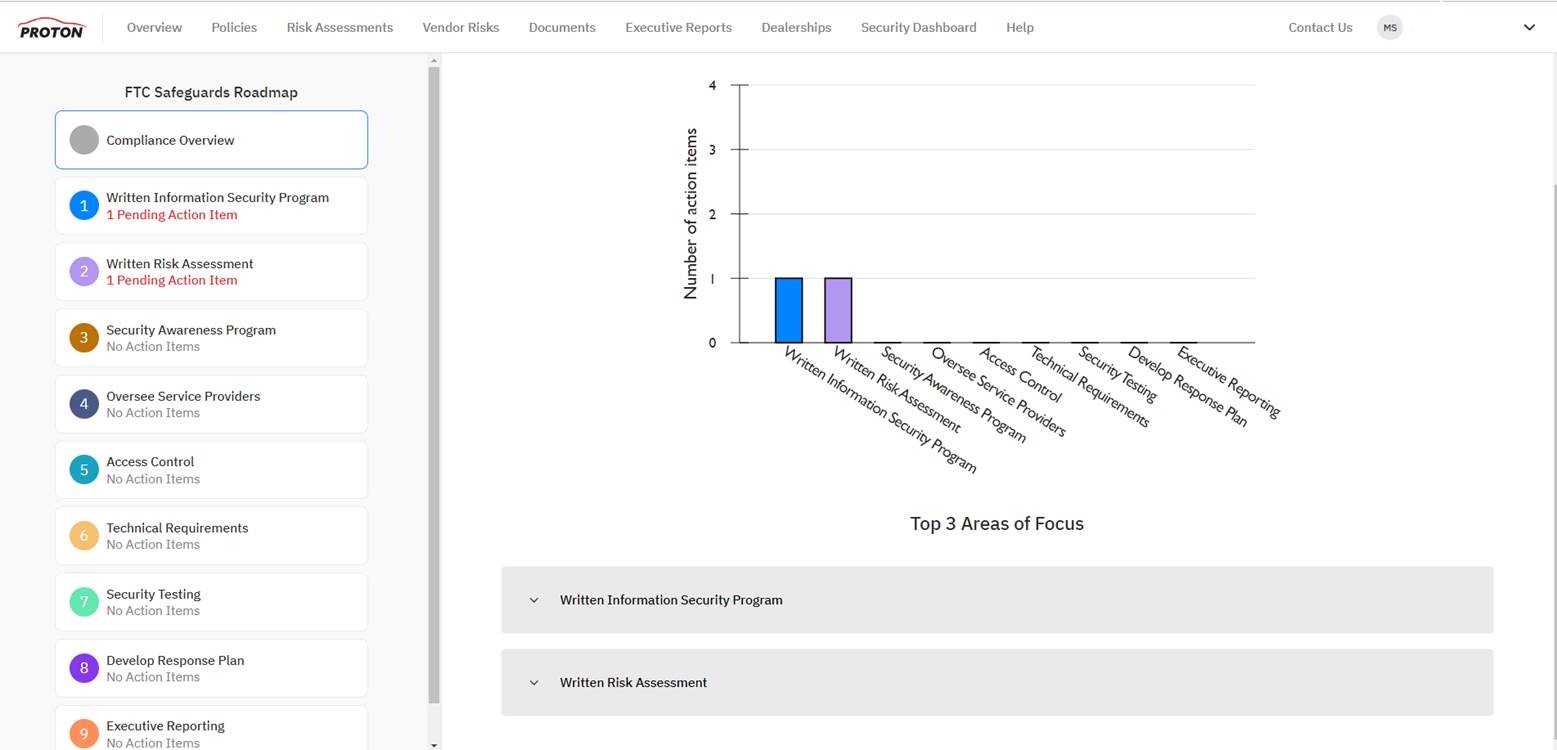
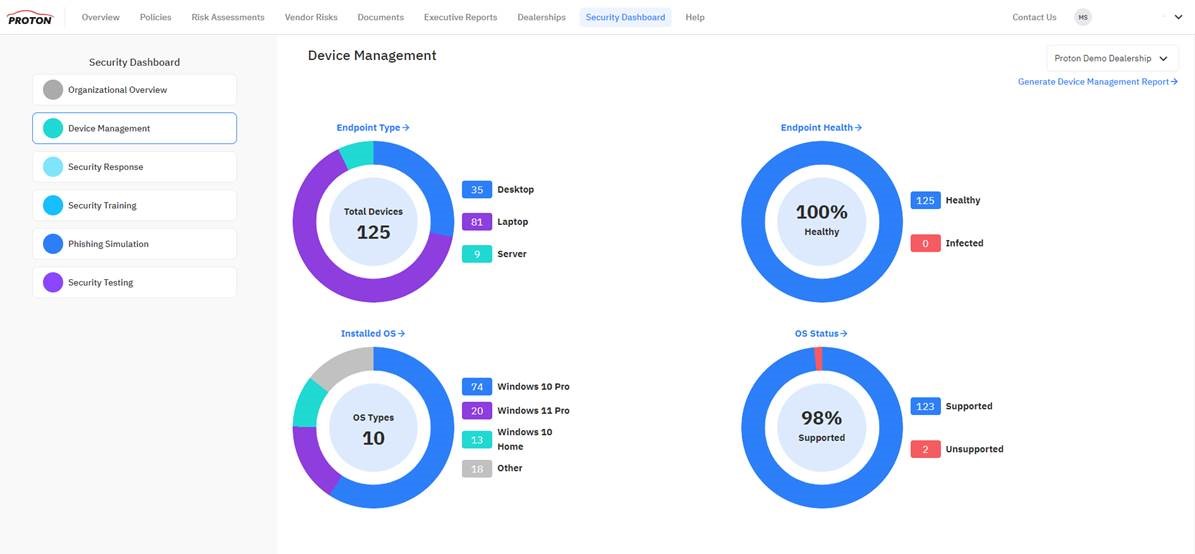
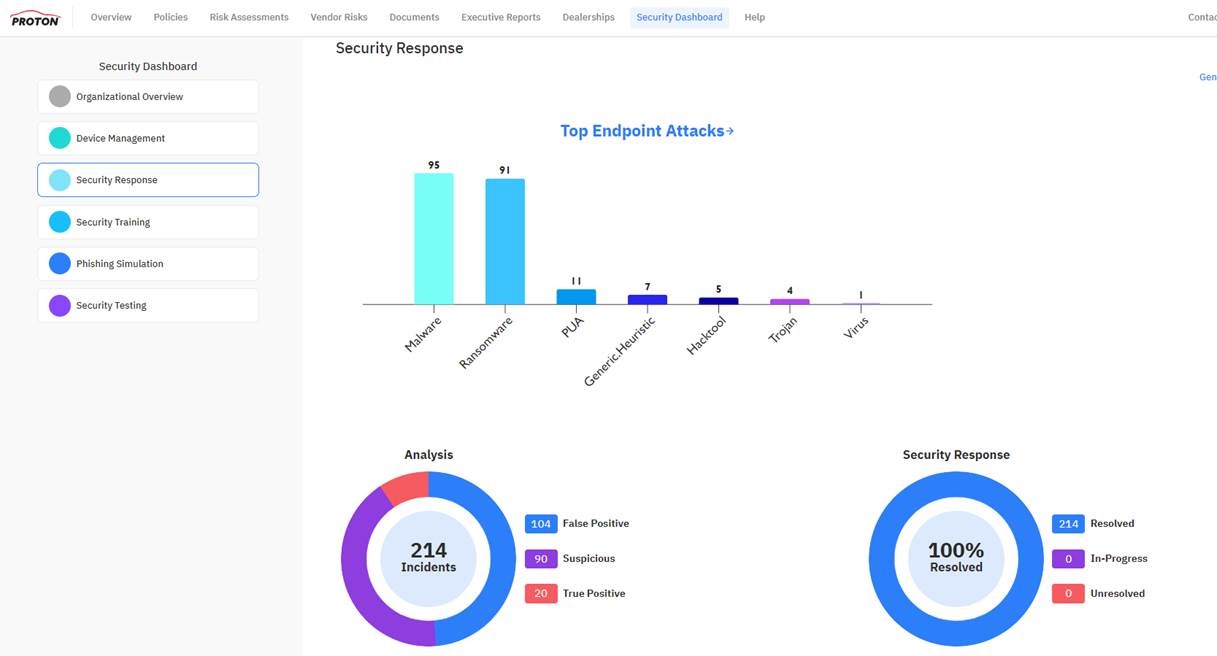
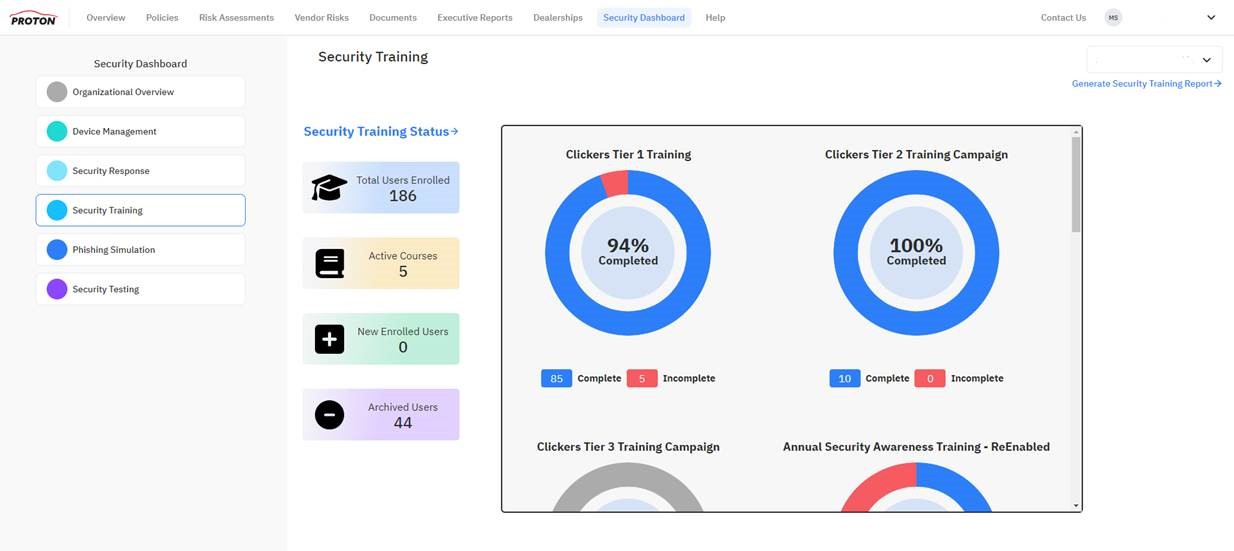
Identity Theft: Real or just in the movies?
Once upon a time, technical attacks were a dealership’s biggest foe. But more and more, cybercriminals rely on stolen identities to gain access to an organization’s systems. In fact, 80 percent of attacks involved compromised identity or credentials. Here are the common identity-based attacks that could be threatening your dealership: